Lawyers increasingly rely on the cloud to store, share, and synchronize their client files. Many use Dropbox and Google Drive for this purpose. However, the use of these common cloud storage services presents some data security concerns. Issues of whether data is encrypted and who has access to the data make some lawyers understandably nervous about having a third party store their client information. The risk of malpractice exposure if client data is compromised or breached is something lawyers need to evaluate.
Before you choose to store your client data with an online third-party vendor, take some time to understand how that data is secured and protected. Encryption, which makes data unreadable, plays a big role in data protection. Data can be encrypted at several levels, but not all vendors encrypt data at every crucial level. A good cloud storage provider encrypts your data at three different stages to provide the most protection: (1) before it leaves your computer, (2) in transit to the provider’s server, and (3) when it is stored on the provider’s server.
My goal is to help you understand why encryption at each stage of data transfer is important. Then you can make an informed decision as to which provider to use. So let’s look at the different stages in more detail without getting too technical.
First stage: Client-side encryption for data before transit
Before you transfer your data from your computer to the provider’s server at their data center, you encrypt your data locally on your hard drive with a private encryption key using the provider’s tool. You are the only one with the key. A copy is not shared with the provider, so it has “zero knowledge” of your key. Without knowledge of your key, the provider has no access to the data stored on its server. This is called client-side or zero-knowledge encryption. Encryption at this level is crucial because it makes all your files unreadable by everyone. Only you can decrypt the data using your key. The data is therefore protected against backdoor access and outside hackers because your key is not stored with the provider.Second stage: Encryption for data in transit
Once your data is locally encrypted on your computer, it will be transferred to the provider’s remote server. The transfer occurs over encrypted connections established by the provider. Encryption at this stage ensures your data is not vulnerable to interception while it’s in motion. Client-side encryption doesn’t prevent attackers from intercepting the transfer and seizing your encrypted data. Even though attackers may not be able to decrypt your data, they can still hold it hostage. In-transit encryption prevents this from happening and provides another layer of security for your data.Third stage: Server-side encryption for data at rest
When your data reaches the provider’s server where it will reside for an indeterminate period, it is secured with a third layer of encryption. Encryption at this stage is done by the provider. It stores and maintains the decryption key along with your data. This is called server-side encryption. Although the provider manages the decryption key at this stage, your data is still protected from provider access as long as you’ve used client-side encryption at the first stage.Below is an illustration of what encryption looks like at the three stages and what it looks like when there is no client-side encryption at stage 1.
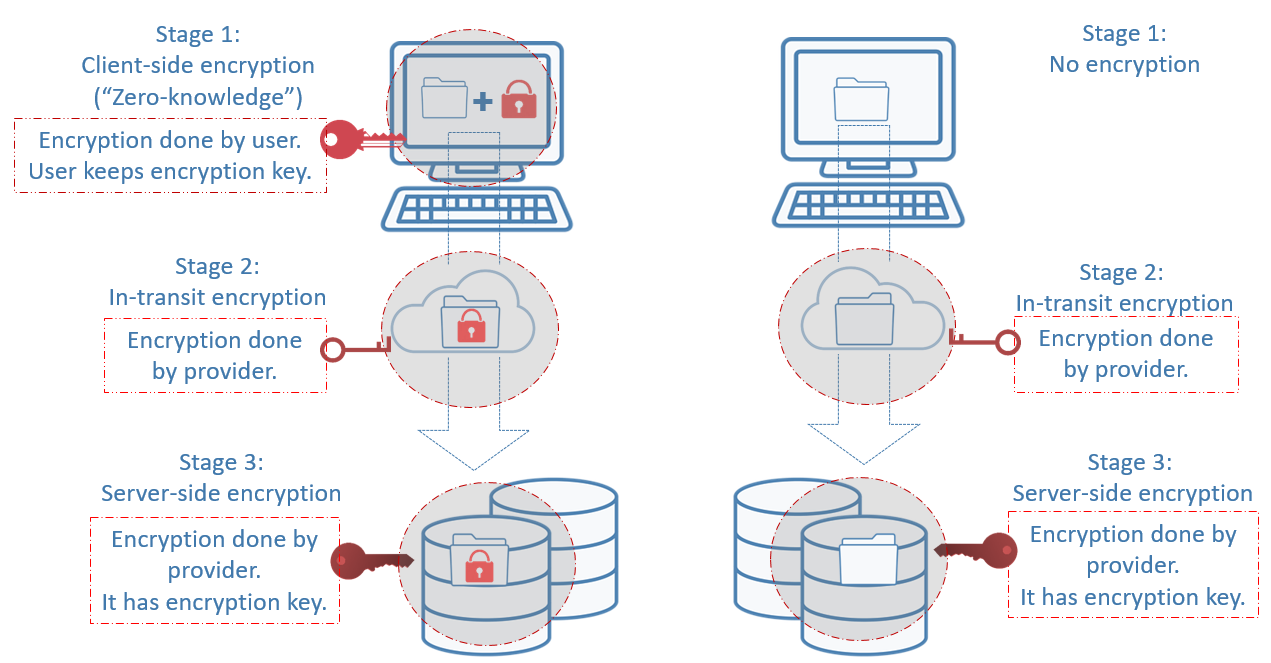
What does this mean for lawyers?
Almost all cloud storage providers offer encryption at the second and/or third stage. Only a handful offer encryption at all three stages.This means that storage providers (e.g. Dropbox and Google Drive) who do not offer client-side encryption have the ability to access your data. This is something you want to seriously think about if you’re storing sensitive or confidential client information on their servers.
What are your options?
You have many options to better protect your client data stored online. Below are a couple of practical options for lawyers.
Use zero-knowledge providers
Zero-knowledge cloud storage providers use encryption at all three crucial stages. Client- side encryption at the first stage lets you manage your own key. The upside of this is obvious: providers have no access to your data. The downside, however, is that if you lose or forget your key, your data is gone. You can’t rely on the providers to reset the password for you or issue you a new password. They only have proof that you have your key, but they don’t have the key itself. Other downsides include slow backup and recovery due to security measures in place.
If you want to use zero-knowledge storage providers, here are some you can look into: SpiderOak (U.S.), Terosit (Switzerland) Sync.com (Canada), pCloud (Switzerland), and MEGA (New Zealand).
Encrypt before you upload
If you choose to use Dropbox or a storage provider that doesn’t offer client-side encryption, you should consider using third-party zero-knowledge software to locally encrypt the data yourself before you upload to the cloud. When you use the encryption software, only you, not the software provider, have the key to decrypt the files. Once the encrypted files are uploaded to the storage provider’s server, there is no risk that it can access your data.
After downloading the software, you will set up your account and select Dropbox or whomever your cloud storage provider is. An encrypted drive connected to Dropbox will be created on your computer. When you transfer files to the encrypted computer drive, those files will be automatically encrypted and then uploaded to Dropbox through file synchronization. They will be stored there in their encrypted state. Beware that some user features such as file sharing may be limited when your data is encrypted.
Here are a few software programs that offer zero-knowledge encryption: Boxcryptor, ODrive, and Cryptomator Many other programs allow you to encrypt before uploading, but they are not zero-knowledge. They include NCrypted Cloud, Sookasa/Safemonk, and Safebox.
Always vet the vendors
Do your due diligence by vetting the providers. Research their reputation by reading online reviews and articles about them. See how long they have been in business and whether they serve lawyers. Review the terms of service and user agreement to ensure they comply with industry standards for preserving confidentiality and security of data. Use the resources below to help you do the vetting.Resources:
- Online Data Storage Providers – PLF Practice Aid
- Encryption Made Easy: The Basics of Keeping Your Data Secure – OSB Bar Bulletin Article


















_dragonwithlaptop1681501312-18359.jpg)



